Research Library
The top resource for free research, white papers, reports, case studies, magazines, and eBooks.
- Information Technology
- Data Infrastructure
- Data Tools
- Desktops, Laptops and OS
- Chip Sets
- Collaboration Tools
- Desktop Systems - PCs
- Email Client
- Embedded Systems
- Hardware and Periferals
- Laptops
- Linux - Open Source
- Mac OS
- Memory Components
- Mobile Devices
- Presentation Software
- Processors
- Spreadsheets
- Thin Clients
- Upgrades and Migration
- Windows 7
- Windows Vista
- Windows XP
- Word Processing
- Workstations
- Enterprise Applications
- IT Infrastructure
- IT Management
- Networking and Communications
- Bluetooth
- DSL
- GPS
- GSM
- Industry Standard Protocols
- LAN - WAN
- Management
- Mobile - Wireless Communications
- Network
- Network Administration
- Network Design
- Network Disaster Recovery
- Network Interface Cards
- Network Operating Systems
- PBX
- RFID
- Scalability
- TCP - IP
- Telecom Hardware
- Telecom Regulation
- Telecom Services
- Telephony Architecture
- Unified Communications
- VPNs
- VoIP - IP Telephony
- Voice Mail
- WAP
- Wi-Fi (802.11)
- WiMAX (802.16)
- Wide Area Networks (WAN)
- Wireless Internet
- Wireless LAN
- Security
- Servers and Server OS
- Software and Web Development
- .Net Framework
- ASPs
- Application Development
- Application Servers
- Collaboration
- Component-Based
- Content Management
- E-Commerce - E-Business
- Enterprise Applications
- HTML
- IM
- IP Technologies
- Integration
- Internet
- Intranet
- J2EE
- Java
- Middleware
- Open Source
- Programming Languages
- Quality Assurance
- SAAS
- Service-Oriented Architecture (SOA)
- Software Engineering
- Software and Development
- Web Design
- Web Design and Development
- Web Development and Technology
- XML
- Storage
- Agriculture
- Automotive
- Career
- Construction
- Education
- Engineering
- Broadcast Engineering
- Chemical
- Civil and Environmental
- Control Engineering
- Design Engineering
- Electrical Engineering
- GIS
- General Engineering
- Industrial Engineering
- Manufacturing Engineering
- Materials Science
- Mechanical Engineering
- Medical Devices
- Photonics
- Power Engineering
- Process Engineering
- Test and Measurement
- Finance
- Food and Beverage
- Government
- Healthcare and Medical
- Human Resources
- Information Technology
- Data Infrastructure
- Data Tools
- Desktops, Laptops and OS
- Chip Sets
- Collaboration Tools
- Desktop Systems - PCs
- Email Client
- Embedded Systems
- Hardware and Periferals
- Laptops
- Linux - Open Source
- Mac OS
- Memory Components
- Mobile Devices
- Presentation Software
- Processors
- Spreadsheets
- Thin Clients
- Upgrades and Migration
- Windows 7
- Windows Vista
- Windows XP
- Word Processing
- Workstations
- Enterprise Applications
- IT Infrastructure
- IT Management
- Networking and Communications
- Bluetooth
- DSL
- GPS
- GSM
- Industry Standard Protocols
- LAN - WAN
- Management
- Mobile - Wireless Communications
- Network
- Network Administration
- Network Design
- Network Disaster Recovery
- Network Interface Cards
- Network Operating Systems
- PBX
- RFID
- Scalability
- TCP - IP
- Telecom Hardware
- Telecom Regulation
- Telecom Services
- Telephony Architecture
- Unified Communications
- VPNs
- VoIP - IP Telephony
- Voice Mail
- WAP
- Wi-Fi (802.11)
- WiMAX (802.16)
- Wide Area Networks (WAN)
- Wireless Internet
- Wireless LAN
- Security
- Servers and Server OS
- Software and Web Development
- .Net Framework
- ASPs
- Application Development
- Application Servers
- Collaboration
- Component-Based
- Content Management
- E-Commerce - E-Business
- Enterprise Applications
- HTML
- IM
- IP Technologies
- Integration
- Internet
- Intranet
- J2EE
- Java
- Middleware
- Open Source
- Programming Languages
- Quality Assurance
- SAAS
- Service-Oriented Architecture (SOA)
- Software Engineering
- Software and Development
- Web Design
- Web Design and Development
- Web Development and Technology
- XML
- Storage
- Life Sciences
- Lifestyle
- Management
- Manufacturing
- Marketing
- Meetings and Travel
- Multimedia
- Operations
- Retail
- Sales
- Trade/Professional Services
- Utility and Energy
- View All Topics
- Featured eBooks
- Trending Resources
- New Resources
- Promote Your Content
- Partnership Opportunities
- Get RSS Updates
- About TradePub.com
- FAQ
- Contact Us
Share Your Content with Us
on TradePub.com for readers like you. LEARN MORE
Request Your Free Infographic Now:
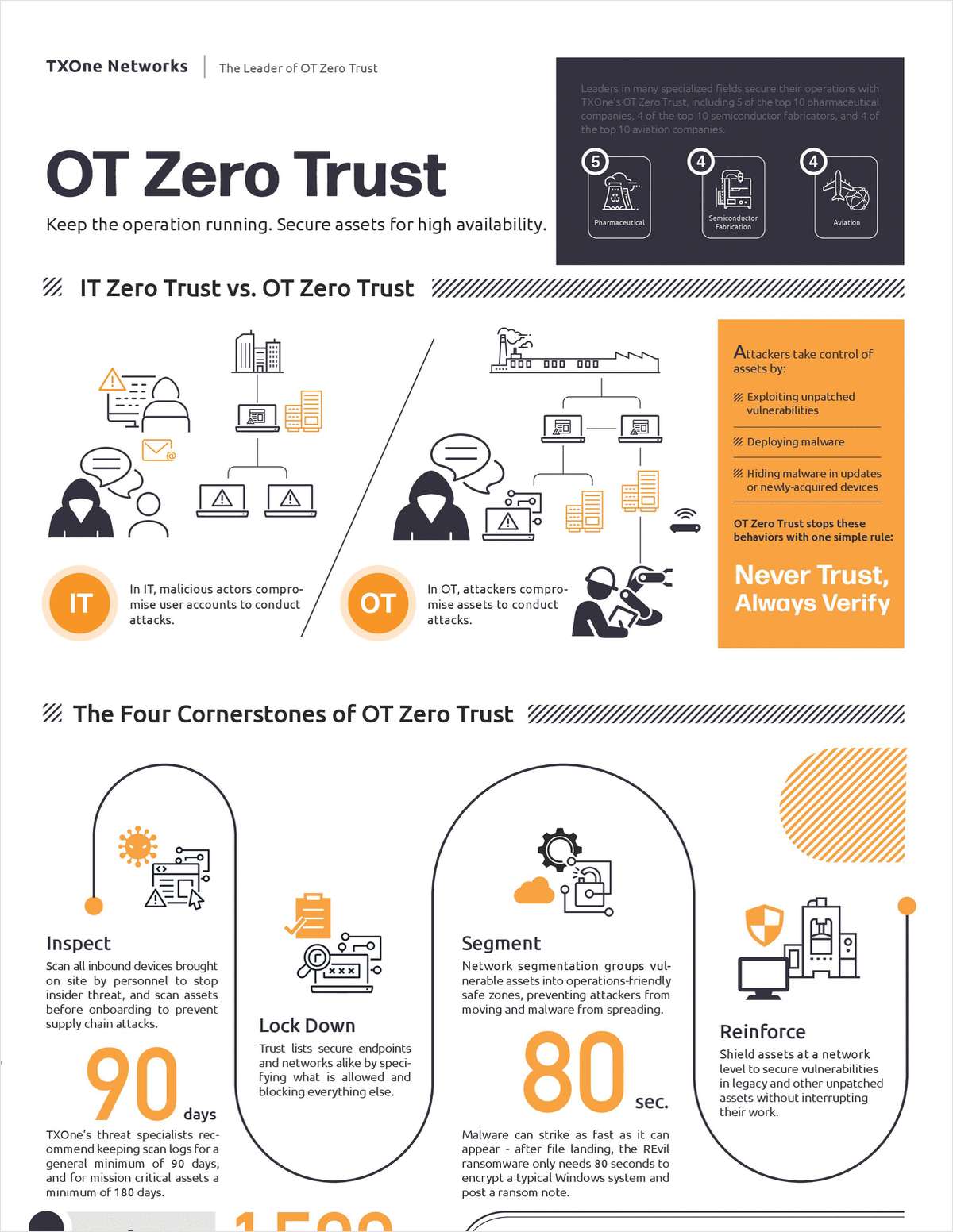
"IT Zero Trust vs. OT Zero Trust: It's all about Availability"
Keep the Operation Running. The philosophy of OT zero trust was developed as an answer to the problems traditional cyber defenses create in OT environments. See the differences below.
The philosophy of OT zero trust was developed as an answer to the problems traditional cyber defenses create in OT environments. IT cybersecurity uses a priority system called “CIA” - confidentiality first, integrity second, and availability third. OT network security, on the other hand, is based on asset activity so that productivity can always be the highest priority.
This requires a different model, “AIC” - availability is #1, integrity is #2, and confidentiality is #3. The OT Zero Trust approach prepares cyber defenses to never make assumptions about credibility and to continually evaluate trust on the network.
Offered Free by: TXOne Networks
See All Resources from: TXOne Networks